One such mitigation approach is continuous authentication, which is a user-friendly method of maximizing control throughout any online session. It provides extensive initial security sign-on protection, but also continuously assesses cybersecurity risks and invokes additional processes to offset them. Internal auditors need to understand continuous authentication, including its benefits and challenges.
The Growing Cost
The COVID-19 pandemic established a new paradigm in the way most organizations do business. Many instantly became more virtual, with employees working from home, vendors and customers interacting digitally, and more and more data being stored in the cloud. As online presence grew, it also ushered in increased risks from unauthorized and nefarious users, leading to data theft, ransomware attacks, and destruction of resources.
According to the Identity Theft Resource Center, the U.S. had 3,205 data compromises in 2023— 1,404 more than in 2022. Healthcare, financial services, professional services, manufacturing, and education were the sectors attacked most often. Cybersecurity experts warn the number of breaches will continue to grow.
In 2023, the average cost of a data breach reached an all-time high of $4.45 million, the Ponemon Institute reported. Fines and settlements against companies such as Google Ireland, Morgan Stanley, Uber, Capital One, Home Depot, Meta, T-Mobile, TikTok, Instagram, Equifax, Amazon, and Didi Global exceed $4.4 billion. This is convincing evidence that the threat from unauthorized access is significant and must be controlled.
Traditional Access Control
The traditional approach to controlling user access has been pairing user IDs and passwords. This approach is easy to implement and maintains a moderate level of control. As threats have grown, however, organizations have adopted more complex password requirements, including longer passwords that use special characters, numbers, and capitalization and are updated more frequently.
The next level of access control involves multifactor authentication (MFA). MFA goes beyond entering an ID and password to using a combination of controls for much more enhanced security. MFA requires some combination of:
- What the user knows (ID, password).
- What the user has (smartphone, authentication device).
- Who the user is (fingerprint, facial recognition).
For example, a user might access a system with a unique user ID and password and then enter a code on a handheld device such as a smartphone. This example illustrates the use of something the user knows (the ID and password) and something the user has (the smartphone). Other authentication methods, such as facial recognition, can be introduced, providing even more security.
MFA does have limitations, however, and they are becoming more pronounced because of the tenacity and sophistication of attacks. Such limitations include:
- Phishing. Nefarious players can use various phishing techniques to gain access to initial sign-on credentials as well as the other factors.
- One-time authentication. Once a user is authenticated, he or she continues the session and remains in the system without additional verification.
- Subsequent threats. Once authenticated into a session, a user could browse sensitive data or disable security functions, such as firewalls, without being detected.
Thus, although MFA is a positive development for data security, it cannot prevent all cybersecurity breaches.
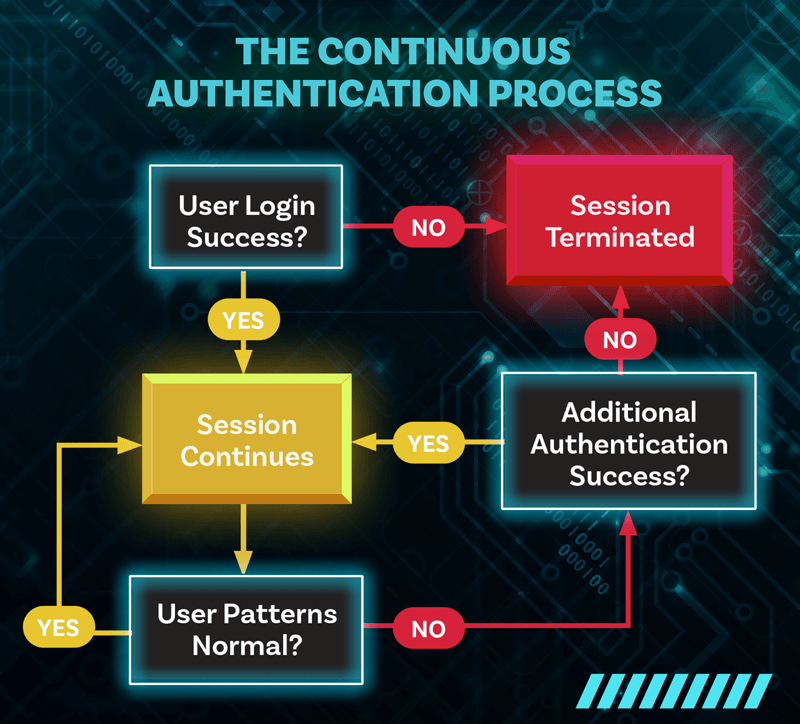
Continuous Authentication
Continuous authentication is a security approach that moves well beyond MFA. It uses traditional methods for initial access but then uses other novel and contemporary controls to continuously provide assurance that the user is, indeed, still authorized to access the system.
As shown in “The Continuous Authentication Process” on this page, continuous authentication is more a process than a single event. It begins with the user accessing the system using a traditional method, such as an ID/password pairing or, preferably, MFA. The system then monitors the user with various technical and biometric measures. If the user behaves according to normal patterns, then the session continues. However, if the system notices a change in the user or the user’s patterns, then it invokes other techniques to validate the user. If these other techniques fail, the session can be terminated.
Continuous authentication can be highly effective without being intrusive. For example, once a user is initially logged into the system, the continuous authentication process can invoke such technologies as:
- Facial recognition. This method quickly scans the user’s face and maps the features to stored data, thereby allowing the system to recognize the user.
- Mouse movements. Each user moves the mouse in unique and predictable ways, including speed, pattern, and velocity. Such patterns can be stored and then occasionally compared to the user’s movements, or the system can simply recognize changes in mouse movement behavior.
- Data access changes. Upon initial sign-on, a user is typically granted access to certain data sources based on an access matrix. The system can monitor access and determine if the user is only accessing authorized data.
- User device dynamics. If users are holding a handheld device or a smartphone, they will have certain ways they interact with that device, such as holding it at unique angles. These patterns could be stored, or the system could simply recognize changes in those patterns.
- Date and time patterns. Some users have certain days, and even certain times of day, when they log onto the system. For example, a user might typically log in during the evening or possibly only on weekdays. Any changes to this pattern could be suspicious and therefore trigger additional security measures.
- Location tracking. The system can detect a change in the user’s physical location, signaling the possibility the user has been impersonated during a session. Also, some users may have a pattern of logging in from a particular city or region, and the system could flag the user if logging in from a different location. This does not mean the user could not log in; the system just may require additional measures.
- System environment scan. On original sign-on, each user is often granted permission to certain data sources. A user could then attempt to get into other areas, and an occasional scan could verify if the access is in keeping with the original intent.
- Keyboard patterns. Each user has a unique way of interacting with the keyboard — certain typing speeds and rhythms and even predictable ranges of pressure on the keys. Any change in these patterns could signal the possibility of a different user impersonating the original, authenticated user.
Significant Benefits
Continuous authentication provides significantly enhanced security because of its use of novel control methods and its ongoing authentication process. Another profound benefit is enhancing the user experience. When implemented correctly, the authentication process is seamless and barely noticeable by the user. This is a significant improvement over requiring the user to constantly re-enter authorization credentials.
Continuous authentication also can reduce costs. When relying primarily on passwords, organizations typically require frequent password changes and lock out the user after a specified number of failed attempts. Without the need for frequent credential changes and with a lower risk of lockouts, the user’s experience is better, and the organization reduces costs by not needing to administer and monitor these processes. Also, fewer lockouts enhances productivity.
Many regulatory frameworks, including the U.S. Health Insurance Portability and Accountability Act and the European Union’s General Data Protection Regulation, require organizations to have robust cybersecurity controls. By invoking continuous authentication, organizations are more likely to be in compliance with such regulations.
Potential Challenges
Continuous authentication is a significant improvement for cybersecurity; however, it does have its challenges. One of the foremost concerns is data privacy. An effective continuous authentication strategy relies on behavioral and biometric pattern recognitions, which could raise privacy concerns.
Additionally, these systems can rely on sophisticated sensors and algorithms, which can have technical challenges. They can be expensive, difficult to implement, and problematic to maintain. Users may be reluctant to adopt continuous authentication systems if they see them as unnecessary or overly intrusive.
Internal Audit and Continuous Authentication
Continuous authentication can provide greater security for virtually any organization. It also can directly benefit internal audit functions through:
- Enhanced risk management. Internal audit can assess how well the continuous authentication process is working. It can review authentication logs to assess system risks and possibly mitigate future risks by suggesting enhanced techniques or parameters.
- Greater compliance. As noted previously, continuous authentication provides greater compliance with certain data security regulations. Auditors also can use continuous authentication data to determine the vulnerability of sensitive data and suggest ways to enhance the security of that data.
- Better fraud identification. When continuous authentication systems identify certain types of unauthorized access, those systems can respond by locking out unauthorized users. Internal auditors can have certain types of activities flagged that may signal someone is considering committing a fraud.
- Streamlined audit process. Perhaps the greatest benefit to internal auditors is the ability to streamline the audit process, itself. Continuous authentication processes maintain logs that can be useful for auditors. Such logs can provide information about timing and nature of data and system access. Rather than generating their own reports, auditors can rely on such data to streamline the audit process. They also can review real-time monitors for greater control and security.
A Seamless Approach
Continuous authentication can significantly enhance organizational cybersecurity by invoking a combination of traditional sign-on methods, MFA, and behavioral and biometric pattern recognition. As with most such technologies, it is evolving in flexibility and sophistication, with artificial intelligence likely to bring about rapid changes to its capabilities. When implemented correctly, continuous authentication provides a seamless, highly effective way to authenticate users and monitor their behavior and access according to that authorization.




